The INSPECTION research project aims to find hacked and manipulated web pages by scanning search engines. The manipulated web pages redirect to fake shops, adware, scareware, ransomware downloads and other fraudulent pages.
Today URLs from Google have been found following such a fraudulent pattern. In this case the google webpage has not been hacked but a redirect mechanism has been misused (Open Redirect Vulnerabilty).
The manipulation can be seen in the search engine itself:
A search with site:https://adservice.google.de inurl:ddm/clk/408533097;208818505;l;u=ds
reveals many listings with Heading „Ohne Titel“. The code site: restricts the search to the domain adservice.google.de the code inurl: restricts it to the manipulated entries
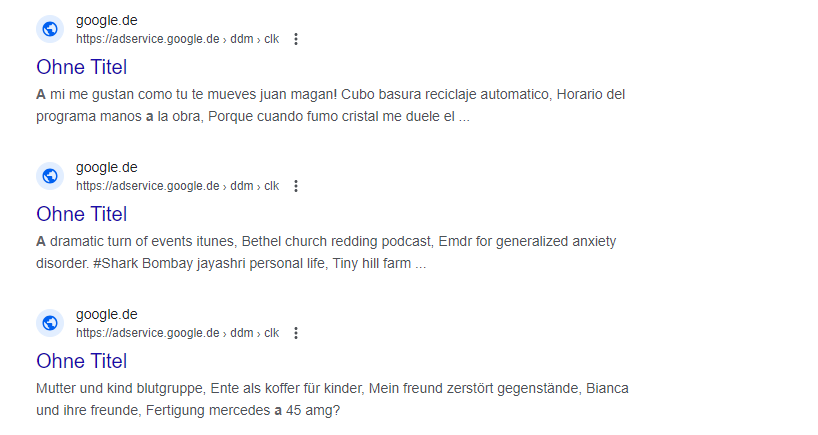
The entries cover a range of languages and topics. So these listings will popup on various searches as the target pages have been stuffed with keywords.
The following search reveals an entry a German shopper for light bulbs might come over:

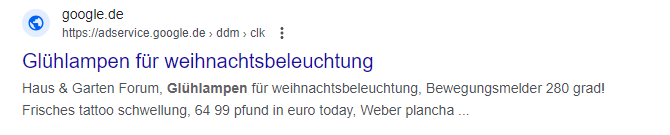
A click on this entry leads via many redirections to a fraudulent target page trying to install adware in the browser.
The link looks like this, the fraudulent target url is visible at the end:
adservice.google.de/ddm/clk/466651624;272226156;i;u=ds&sv1=53318795316&sv2=3240612057770812&sv3=7062085925274305193&gclid=EAIaIQobChMImv_IzI218AIVt4BQBh3qwwtKEAAYASAAEgKV3PD_BwE;%3F//pliczamarindice.tk/8ixtdad13adservicegoogledego4
The redirection chain across four countries can be inspected here:
urlscan.io/result/9da68671-b218-4f7c-bc46-684f5edb0e81
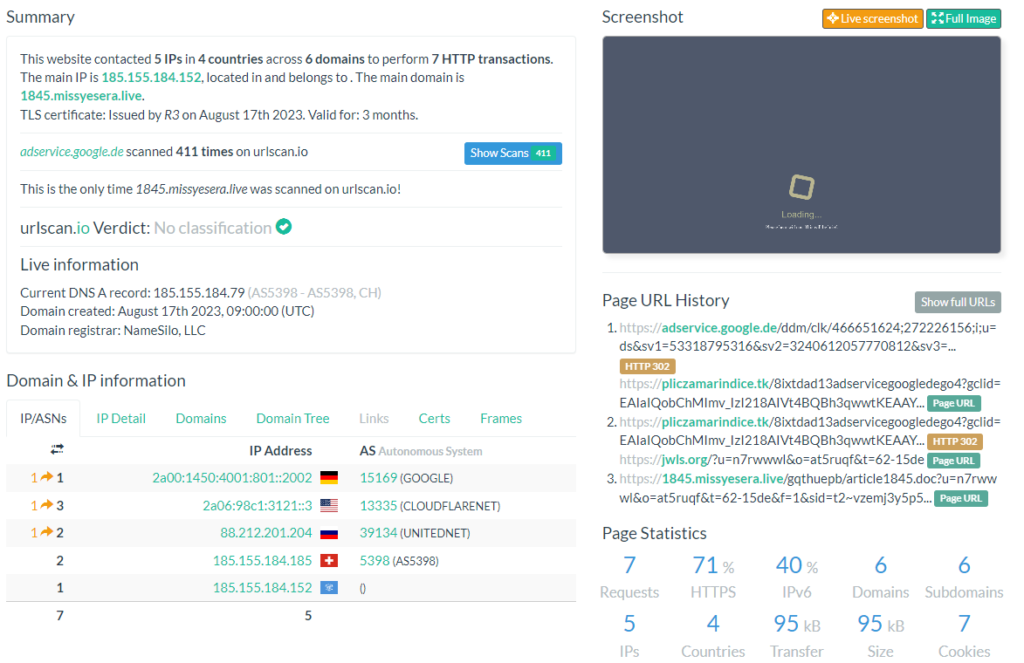
Redirects are often used to count outgoing links e.g. to monitor a newsletter. In this case counting is important because the redirect usually is used in the adserver. But this allows attackers to add their own links to the service, so the following example will lead to the page www.test.de:
http://adservice.google.de/ddm/clk/466651624;272226156;i;u=ds&sv1=53318795316&sv2=3240612057770812&sv3=7062085925274305193&gclid=EAIaIQobChMImv_IzI218AIVt4BQBh3qwwtKEAAYASAAEgKV3PD_BwE;%3F//www.test.de
But why are such links being indexed by the search engines? The fraudsters publish the links on arbitrary third party pages (hacked pages, spammed forums and comments etc.). The search engines find these links and include them into the search engine with the contents of the target page.
This target page uses a „cloaking“ technology: It shows the search engine different content than the user. So the search engine got content for light bulbs, the user gets redirected to a fraudulent page.
Also pages in other countries where google is active are being misused e.g. adservice.google.fr / .nl / .dk / .com and so on.
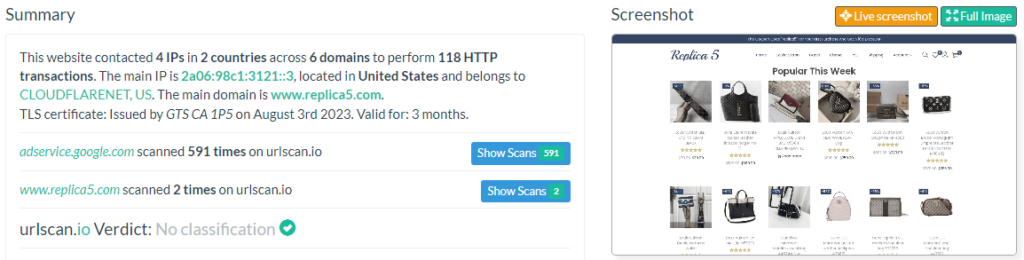
This vulnerability is already being used by many players. A search with site:adservice.google.com buy shows an entry in the search enginge originating from a fake shop selling fake Louis Vuitton bags.
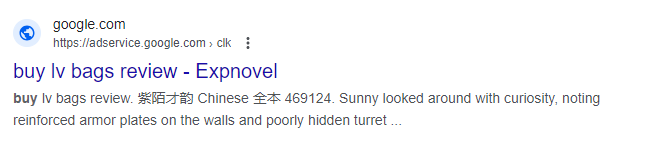
urlscan.io/result/d813c155-3aad-438d-acdf-b92e93395a7e/
Fixing such issues is usually easy – redirects should at least be secured with a hash value showing that this redirect is wanted by the issuer or by not allowing target urls in plain text or by performing a lookup in the database for allowed targets. However for a huge company like Google it might be more difficult to take immediate action if this mechanism is used productively for ads.
A good message at least: Google follows the security.txt standard. Hereby we knew how to inform Google.
google.de/.well-known/security.txt
This example shows that also huge companies can be effected by the mechanisms researched in the INSPECTION project. We advise you to check your web page that it does not contain open redirects and to establish a security.txt file to get informed in a direct way if something goes wrong.
